Consider the following scenario. It’s beyond ten o’clock in the evening. Maybe you opened your laptop one final time to check your email. This time, though, something is awry, if you’re looking for the term “Prevent Ransomware Attack.”, read this article.
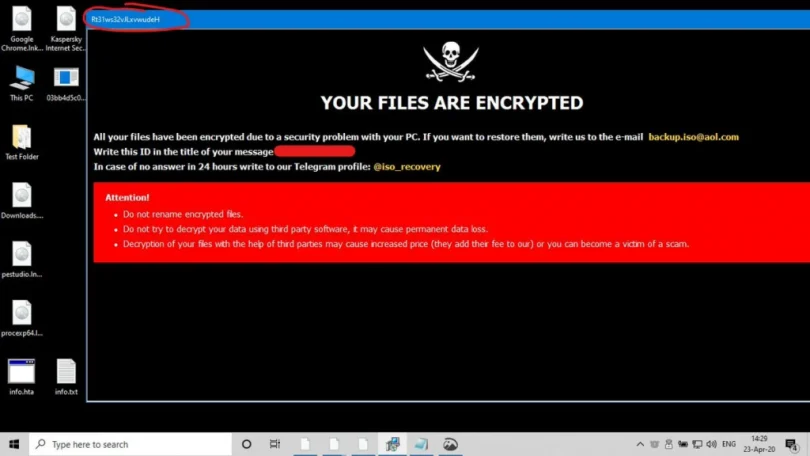
It’s a slow process. The files will not open. On your Windows system, you’re receiving error messages like “unknown file type” or “no related program” if you’re a Mac user. Or perhaps you’ve already been locked out.
The phone then rings. Your IT staff calls, and you hear the words you prayed to the IT gods not to hear: “We’ve been penetrated.”
You return your gaze to your laptop, where it remains in black and white (and usually red).
Ransomware attacks have increased in frequency and severity in recent years. An assault on a company’s network that encrypts critical data may cost hundreds of thousands of dollars, if not millions of dollars. According to Bitdefender’s newest Threat Landscape Report 2020, the overall number of worldwide ransomware complaints grew by 485 percent year over year in 2020.
Ransomware is a serious danger to organizations across all industries, with some sectors, such as education and healthcare, being particularly severely affected. According to a study from Emsisoft, a security solutions company, ransomware hit 1,681 schools and 560 healthcare facilities in 2020.
What Is Ransomware, and How Does It Work?
Ransomware is usually transmitted through spam, phishing emails, or social engineering. It may also infect an endpoint and enter a network by way of webpages or drive-by downloads. Infection tactics are continuously developing, and there are a plethora of ways to infect one’s technology (see section six, “How to Prevent a Ransomware Attack”). Once installed, the ransomware encrypts all files it can access and locks them. Finally, in order to decrypt the files and restore full functioning to the infected IT systems, the virus demands a ransom (typically in Bitcoin).
Typical Ransomware Attack Steps
The following are the typical steps in a ransomware attack:
1. Infection: The ransomware installs itself on the endpoint and any network devices it can access after being transmitted to the system through email attachment, phishing email, infected program, or other way.
2. Secure Key Exchange: To produce the cryptographic keys that will be used on the local system, the ransomware connects with the hackers behind the attack’s command and control server.
3. Encryption: The malware encrypts any data it finds on local computers and across the network.
4. Extortion: Once the encryption is complete, the ransomware shows extortion and ransom payment instructions, threatening data destruction if payment is not made.
5. Decryption: Companies can pay the ransom and hope that the hackers decrypt the files, or they can try to recover data by removing infected files and computers from the network and restoring data from clean backups. Negotiating with cyber thieves is typically futile, as a recent study revealed that 42% of businesses who paid a ransom did not get their files encrypted.
How to avoid a Ransomware Infection (“Prevent Ransomware Attack.”)
A ransomware assault on a house or company may be disastrous. Important and valuable information might be destroyed, and removing the virus and restoring system functionality can take tens or even hundreds of hours of labor.
Ransomware assaults are always evolving, and attack tactics are becoming more complex. You are not required to be a statistic. You can prevent ransomware from infecting your systems with proper preparation and wise procedures.
Defeating Ransomware: Best Practices
1. Block known payloads from launching using anti-virus and anti-malware software or other security measures.
2. Back up all essential files on a regular basis and isolate them from local and open networks.
3. Users may keep completely air-gapped backups with immutable backup solutions like Object Lock. Within the time range defined by the end-user, the data is fixed, immutable, and cannot be removed. You can swiftly recover uninfected data from your immutable backups, deploy it, and get back to business without interruption if you set immutability on important data.
4. Store data backups in areas unreachable from any possibly affected device, such as unconnected external storage drives or the cloud, to prevent ransomware from accessing them.
5. Download and install the most recent security updates for your operating system and apps from the software providers. To close known vulnerabilities in operating systems, browsers, and web plugins, remember to patch early and regularly.
6. Consider implementing security software to guard against infection on endpoints, email servers, and network systems.
7. Practice good cyber hygiene, such as being cautious when accessing attachments and links in emails.
8. Segment your networks to separate important systems and prevent malware from spreading in the event of an attack. Turn off any network shares that aren’t in use.
9. Remove admin privileges from those who don’t need them. Give people the bare minimum of system rights they require to complete their tasks.
10. As far as possible, limit write rights on file servers.
11. Educate yourself, your staff, and your family on how to prevent malware from infiltrating your networks. Keep everyone up to date on the newest email phishing and human engineering schemes aimed at converting victims into accomplices.
It’s obvious that the best approach to deal with a ransomware assault is to prevent one from happening in the first place. Aside from that, ensuring that your essential data is backed up and inaccessible by a ransomware outbreak will guarantee that downtime and data loss are low, if not non-existent, in the event of an assault.
Have you ever been a victim of ransomware, or do you have a plan to avoid being a victim? Please share your thoughts in the comments section.